FlashBot
FlashBot.
Welcome, premium subscribers! Thank you for subscribing. Your names will be recognised on the next video 😘 TLDR below. This is not financial advice.
General Conclusion
In an emerging environment like Layer 1 blockchain, it is not uncommon to have competitors. For instance, there are many projects calling themselves "Ethereum killers". There is an argument to be made against monopolies in the L1 infrastructure, but it is also about solving different vulnerabilities in Ethereum itself.
What are the Vulnerabilities?
Arbitrage bots front-running the transactions.
What? I tell the Ethereum network that I want to make a transaction. i.e. buying 100 ETH on Uniswap. This action will take some time to confirm. During this period, it goes into this pool called Mempool. There, everyone can see that "hey, Lisa is going to buy 100 ETH. It is not executed yet."
The risk? Because this is public, bots can come in to pre-trade. They are called flashbots. The basically front-run your trade. They execute the trade before you.
How? By paying more fees to prioritise their transactions before yours.
What Is Flashbot?
Bots or network robots are software applications that run automated tasks on the network. Typically, bots perform simple tasks and have a repetitive structure at a much higher frequency than humans can manage. They automatically find, analyse and organise information from web servers at speeds much higher than human speed.
Flashbots are like bots, but built with smart contracts (specifically, Ethereum Blockchain) to perform profitable and fast transactions without going through a human. They are also pre-programmed to repeat preset actions over and over.
Inside The Dark Forest (Mempool) And Hunters (Flashbots)
In the mempool, it's all dark and murky. The flashbots can find the trade and execute before you. And they win.
Dark Forest is an environment in which there are dangerous hunters, and if you are caught, death is likely. A job as a person's position is hunting us. (This is also the concept that inspired the Dark Forest game on Ethereum testnet.)
In Mempool, these clever predators take the form of "arbitrage bots". They keep track of pending transactions and try to exploit the profitable opportunities they create.
The one who understands Flashbots best is smart contract researcher Phil Daian, who along with colleagues wrote Flash Boys 2.0 article and came up with the term "Miner Extractable Value" (MEV).
How? Flashbots look for any transaction that they can profitably front-run by copying it and replacing the address with its own address.
Phil once talked about a "Generalised Frontrunner" flashbot that looks for transactions in Mempool (such as DEX transactions or Oracle update) and tries to pre-run them according to a predefined algorithm. Flashbots look for any transaction that they can profitably front-run by copying it and replacing the address with its own address. They can also execute transactions and copy beneficial internal transactions generated by its execution trace.
Case study 1: Uniswap
An example is Uniswap — can anyone recover Uniswap liqudity tokens that have been accidentally sent to the pair contract itself?
These tokens can be recovered by anyone through the burn function on a Uniswap core contract function, which will measure its own liquidity token balance and burn it, sending the tokens to the address specified by the caller. This is a core part of the planned work of Uniswap v2 (the basic mechanism described in section 3.2 of the Uniswap v2 white paper).
What happens when there is a Flashbot frontrun of the caller?
If the monsters are in the Mempool, they will see, copy, transform, and pre-run your transaction, taking the money before your transaction is approved.
Case study 2: Flash Loan
In the previous article about Flash Loan we included some data on many Flashbot-related hacks. These hacks are so sophisticated and fast that the protocol cannot respond to the changes in time, resulting in many people losing money, the protocol's tokens devaluing, and smart contract auditors getting a bad reputation.
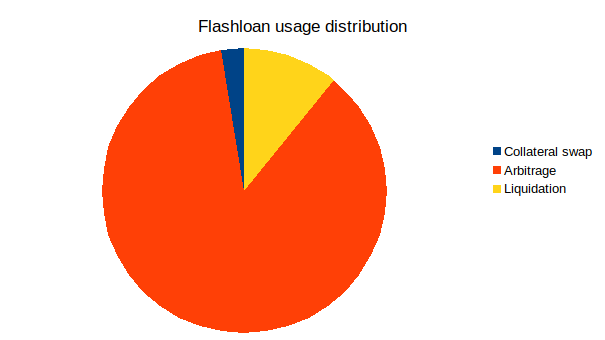
Flash Loans have three main applications: Arbitrage, Collateral Swap, Self-Liquidation.
ⓒEconomics Design
Although there are some good applications in Flash Loans, the danger is that Flash Loans have the ability to attack and hack DeFi applications with millions of dollars in damage each time.
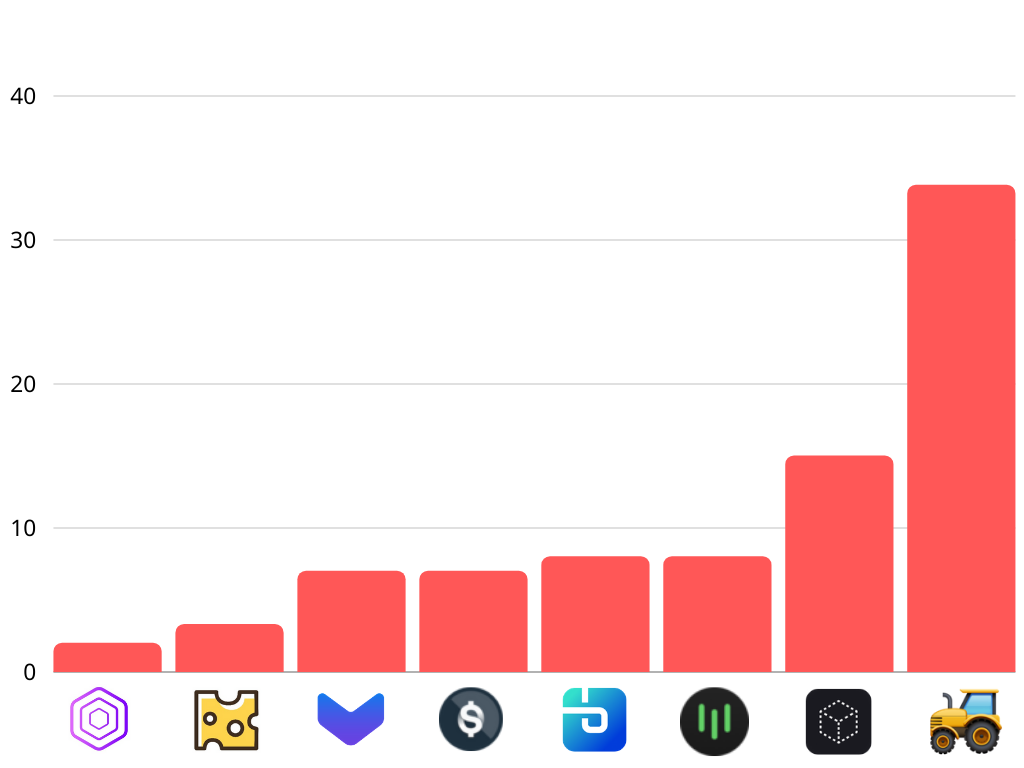
The highest loss recorded so far was to Harvest Finance project (lost $33.8 million).
ⓒCollected by Economics Design
There are two main reasons that Flash Loans are especially attractive to attackers.
Many attacks require a lot of capital in advance (such as oracle manipulation attacks).
Flash loans minimise the risk of disclosure for attackers. If I have an idea of how to manipulate oracle with $10 million ETH, even if I own that much $ETH I may not want to risk my capital. My $ETH will be affected, exchanges can reject my deposits, and the money will be harder to go with. It is quite risky! But if I quickly borrow $10 million, who cares? It is not like dYdX's mortgage pool would be considered as being badly hit, since that is where your loan came from.
Takeaway: Learning Lessons
Hunters Are Real
Hunters (Flashbots) are present on Ethereum Blockchain. There are many solutions to solve these problems but Flashbot still exists.
This is one of the risks in any transaction that we face. There have been pretty good solutions like disorder transactions and designing customised smart contracts. But hunters soon find a way to use these mechanisms to make profits.
Be Careful
Any transactions are followed by Hunters. They will not directly attack you but will choose their prey to capture profits. This is always the case!
Ethereum Blockchain may be a Dark Forest, but it can also be a paradise, depending on the perspective and the precautions. Be careful!
Future
We think in future we can prevent the risks discussed and are delighted that there are already some ambitious efforts to do so. Optimism has a vision of how MEV can be redirected for the benefit of the ecosystem, as part of the layer 2 expansion solution, such as Optimistic Rollups. Starkware, in addition to its own layer 2-scale extension systems, has built a "Verifiable Delay Function" service called Veedo that can make Ethereum apps immune to this type of Frontrun attack (models are used in both Optimism and Starkware).
TLDR:
When discussing about "Ethereum killer", it is not just about fighting the layer 1 tech infrastructure. The truth is that there are risks that needs to be mitigated in this infrastructure. In fact, the attack by flashbots is much higher than 51% attack. Thus, this remains as a real risk in the Ethereum network.